5. Crack WEP (aircrack-ng)
WEP cracking is a simple process, only requiring collection of enough data to then extract the key and connect to the network. You can crack the WEP key while capturing data. In fact, aircrack-ng will re-attempt cracking the key after every 5000 packets.
To attempt recovering the WEP key, in a new terminal window, type:
aircrack-ng data*.cap (assuming your capture file is called data…cap, and is located in the same directory)
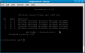 |
aircrack-ng can successfully recover a WEP key with 10-40k captured packets. The retreived key is in hexadecimal, and can be entered directly into a wireless client omitting the “:” separators |
Notes:
If your data file contains ivs/packets from different access points, you may be presented with a list to choose which one to recover.
Usually, between 20k and 40k packets are needed to successfully crack a WEP key. It may sometimes work with as few as 10,000 packets.
6. Crack WPA or WPA2 PSK (aircrack-ng)
WPA, unlike WEP rotates the network key on a per-packet basis, rendering the WEP method of penetration useless. Cracking a WPA-PSK/WPA2-PSK key requires a dictionary attack on a handshake between an access point and a client. What this means is, you need to wait until a wireless client associates with the network (or deassociate an already connected client so they automatically reconnect). All that needs to be captured is the initial “four-way-handshake” association between the access point and a client. WPA hashes the network key using the wireless access point’s SSID as salt. This prevents the statistical key-grabbing techniques that broke WEP, and makes hash precomputation more dificult because the specific SSID needs to be added as salt for the hash.
With all that said, the weakness of WPA-PSK comes down to the passphrase. A short/weak passphrase makes it vulnerable to dictionary attacks.
To successfully crack a WPA-PSK network, you first need a capture file containing handshake data. This can be obtained using the same technique as with WEP in step 3 above, using airodump-ng.
You may also try to deauthenticate an associated client to speed up this process of capturing a handshake, using:
aireplay-ng –deauth 3 -a MAC_AP -c MAC_Client (where MAC_IP is the MAC address of the access point, and MAC_Client is the MAC address of an associated client).
Once you have captured a four-way handshake, you also need a large/relevant dictinary file with common passphrases. See related links below for some wordlist links.
You can, then execute the following command in a linux terminal window (assuming both the dictionary file and captured data file are in the same directory):
aircrack-ng -w dictionary_file capture_file
Notes:
Cracking WPA-PSK and WPA2-PSK may take much longer, and will only succeed with weak passphrases and good dictionary files.
Alternatively, there are tools like coWPAtty that can use precomputed hash files to speed up dictionary attacks. Those hash files can be very effective, but quite big in size. The Church of WiFi has computed hash tables for the 1000 most common SSIDs against a million common passphrases that are 7Gb and 33Gb in size…
Conclusion
As demonstrated above, WEP cracking has become increasingly easier over the years, and what used to take hundreds of thousands packets and days of capturing data can be accomplished today within 15 minutes with a mere 20k data frames.
WPA/WPA2-PSK encryption is holding its ground if using a strong, long key. However, weak passphrases are vulnerable to dictionary attacks. WPA/WPA2 may be on borrowed time as well, according to some recent news.
Related Links
aircrack-ng
Openwall wordlist collection
wordlists – torrent search
the A.R.G.O.N. – wordlists
Church of WiFi hash tables
