3. Capture Data (airodump-ng)
To capture data into a file, we use the airodump-ng tool again, with some additional switches to target a specific AP and channel. Most importantly, you should restrict monitoring to a single channel to speed up data collection, otherwise the wireless card has to alternate between all channels. Assuming our wireless card is mon0, and we want to capture packets on channel 6 into a text file called data:
airodump-ng -c6 bssid 00:0F:CC:7D:5A:74 -w data mon0 (-c6 switch would capture data on channel 6, bssid 00:0F:CC:7D:5A:74 is the MAC address of our target access point, -w data specifies that we want to save captured packets into a file called “data” in the current directory, mon0 is our wireless network adapter)
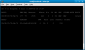 |
Running airodump-ng on a single channel targeting a specific access point |
Notes:
You typically need between 20,000 and 40,000 data packets to successfully recover a WEP key.
One can also use the “–ivs” switch with the airodump-ng command to capture only IVs, instead of whole packets, reducing the required disk space. However, this switch can only be used if targeting a WEP network, and renders some types of attacks useless.
4. Increase Traffic (aireplay-ng) – optional step for WEP cracking
An active network can usually be penetrated within a few minutes. However, slow networks can take hours, even days to collect enough data for recovering the WEP key.
This optional step allows a compatible network interface to inject/generate packets to increase traffic on the wireless network, therefore greatly reducing the time required for capturing data. The aireplay-ng command should be executed in a separate terminal window, concurrent to airodump-ng. It requires a compatible network card and driver that allows for injection mode.
Assuming your network card is capable of injecting packets, in a separate terminal window try:
aireplay-ng -3 -b 00:0F:CC:7D:5A:74 -h 00:14:A5:2F:A7:DE -x 50 wlan0
-3 –> this specifies the type of attack, in our case ARP-request replay
-b ….. –> MAC address of access point
-h ….. –> MAC address of associated client from airodump
-x 50 –> limit to sending 50 packets per second
wlan0 –> our wireless network interface
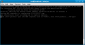 |
aireplay-ng allows for injecting packets to greatly reduce the time required to recover a WEP key |
Notes:
To test whether your nic is able to inject packets, you may want to try: aireplay-ng -9 wlan0. You may also want to read the information available -here-.
To see all available replay attacks, type just: aireplay-ng
